
|
MDM - Mobile Device Management; pro's, con's and best practices
|

|
This page
describes security measures that may be taken by organizations to
protect data, and the impact it may have on subjects.
Goals of Security Measures
Security measures are typically taken to protect sensitive data in
organizations and/or to comply with law. The requirements that the
security of an endpoint must meet:
- The equipment must have encrypted storage, to prevent loss of setting information in the event of theft;
- User does not use USB sticks or external hard drives, unless strictly necessary and only if they are fully encrypted;
- The laptop or desktop is only accessible to the user with the
institution account, or the device is provided with a specific employee
account with a strong password;
- A mobile device (telephone, tablet) is provided with a strong
access code (minimum 6 characters) other than the SIM card PIN code;
- The OS and all applications are maintained by a supplier or community, and are up to date;
- Performing security updates of OS and applications on the equipment are mandatory;
- Anti malware and anti virus solution are present, active and up to date;
- Local (application) firewall is active and alerts the user to unusual behavior. Preferably also with outgoing traffic;
- Laptop or desktop should be automatically locked after a preset period of inactivity after a maximum of 15 minutes;
- Phones or tablets should be automatically locked after a pre-set period of inactivity after a maximum of 5 minutes;
- Equipment must have the ability to remotely wipe the device in the event of loss or theft;
- Deviations from the previous requirements must be detected and reported.
And in general:
- two factor authentication in using (financial) authorization systems
- two factor authentication in using (Microsoft) cloud
- strong passwords
- use of VPN
Organisations typically revert to MDM solutions from particular
vendors to implement and enforce policies. A good description is on
WikipediA:
Using any enforcement system to control and enforce this on
employees requires trust, integrity, benevolence, competence and
reputation. This article says it clearly:
Mobile device management requires a level of trust between the end
users in your organization and the people responsible for managing the
MDM platform. There needs to be clear communication between the parties
to ensure that expectations are properly set. There also needs to be
reasonable policies in place to reduce the risk of administrative error
(or malicious action) causing a data loss or breach of privacy for the
user of a managed device. This means that you should have, at a minimum:
- An acceptance policy for end users who are enrolling devices in
your MDM solution. A real one, written by humans and only partially
mangled by lawyers. The goal is to have a document that your users will
actually read, understand, and willingly sign (or reject), and not just a
formality that gets signed and filed away somewhere to cover your butt
in the event of a problem later.
- A limited number of trusted and trained administrators who can
manage the sensitive and impactful elements of the MDM solution (e.g.
able to configure policies, access inventory data, etc). Limited access
can be provided for support staff to deliver end user support, but like
all administrative rights should be provided on a least privilege basis.
- Privacy advocates from the user population who can review and
understand the level of control and access that the MDM solution
provides over managed devices.
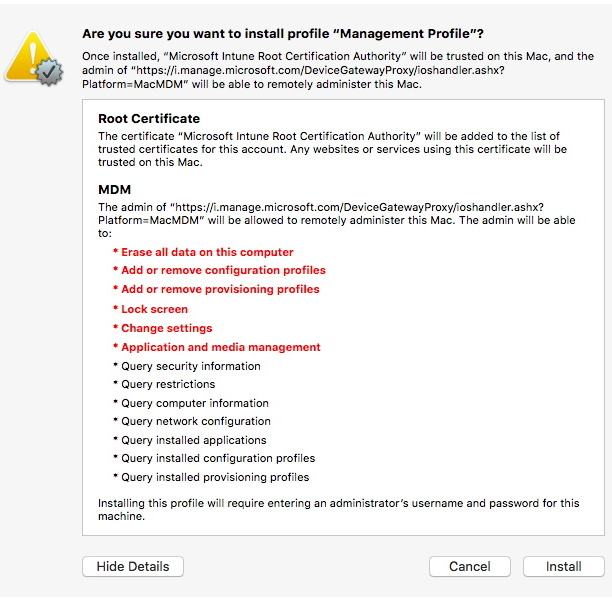
Microsoft InTune on Apple
One popular tool to control company devices is Microsoft InTune. The website for what it does:
- What is device enrollment?
- What information can my organization see when I enroll my device?
- Intune support for new settings and updates in iOS 13 and macOS 10.15
- Enroll your macOS device using the Company Portal app
-
Note:
- Throughout this process, you might be prompted to
allow Company Portal to use confidential information that's stored in
your keychain. These prompts are part of Apple security. When you get
the prompt, type in your login keychain password and select Always
Allow. If you press Enter or Return on your keyboard, the prompt will
instead select Allow, which may result in additional prompts.
- This effectively means it can access all your passwords!
- Also note that after install the profile most likely
locks out the access to certain preference panels, e.g. the ability to
remove profiles, change passwords, manage encryption.
Other hardware related stuff
- Security functionality connected to hardware:
|
|
|
What Can Microsoft Intune See On Your Managed Mobile Devices?
- What Can Microsoft Intune See On Your Managed Mobile Devices?
- note: However there is no additional warning
provided to the user of the device, so they would not know when a device
has been changed from personal to corporate owned by an administrator.
- Intune MacOS management Capabilities
What Can Microsoft Intune with some scripting do Your Managed Devices?
- What Can one do with powershell-intune-samples:
Authoriteit persoonsgegevens & Privacy Issues
- Controle van werknemers
- Bring your own device legal issues
- Werken op waarde geschat: Grenzen aan digitale monitoring op de werkvloer door middel van data, algoritmen en AI
Data Protection Impact Assessment (DPIA) zakelijke microsoft intune dienst; vijf lage privacyrisicos
- Pricacy Company: In opdracht van het Ministerie van Justitie en
Veiligheid heeft Privacy Company onderzoek gedaan naar de privacyrisicos
van het gebruik van de zakelijk Intune software van Microsoft. Daarmee
kunnen systeembeheerders bijvoorbeeld informatie versleutelen op de
apparaten van gebruikers. Privacy Company heeft ook onderzoek gedaan
naar de privacyrisicos van de browserversie van Microsoft Office 365 en
de Office apps voor iOS en Android mobiele telefoons. Met toestemming
van het Ministerie publiceren wij twee blogs over onze bevindingen, deze
blog over Intune:
- en de tweede blog over de browserversie en de app-versie van Office 365:
Never accept an MDM policy on your personal phone
- 20th January 2018 on Security, Infrastructure by Christopher Demicoli
Transparency examples
- Rutgers University Mobile device management policy
NCSC advise when moving to cloud
New links



